Turn on the news and you will see a breach announced for some company. It is happening all the time. In most cases we, as consumers, accept the risk for the convenience of using a credit card for purchases. While there isn’t much you can do to protect your information once you have given it to a business, there are some things you can do to help reduce your risk while shopping online.
Scan for Malware
Most of our online purchases happen from our own computer indicating that this is where we should start our own protections. Over the years we have always told people to make sure you are running anti-virus software, but there are other types of malicious software (called malware) that these programs often don’t detect. Malware is software that is installed on your computer, usually without your knowledge, that has a malicious intent. It may be that it is trying to steal your passwords, credit card information, or other sensitive information. It might be software to spy on you using your computer’s built in microphone or video camera. In any case, it is software that you do not want installed.
There are other programs that you can get to remove this type of malware, above and beyond the use of anti-virus software. A program that I found very useful, that I don’t have any affiliation with, is MalwareBytes (https://www.malwarebytes.org). The greatest benefit is how easy the program is to use (oh and they have a free version). It scans your system for malware and does a really good job of removing it for you. If you have ever tried to remove malware before, it can be pretty difficult. Not with some of these programs like MalwareBytes. If you notice your computer running slow or acting odd it may be a good idea to give it a scan to see if anything comes up.
Be Careful with Emailed Links
Phishing, the art of sending emails with the intent on tricking the user into visiting a malicious site or installing malicious software, is a common way for an attacker to infect your system. All too often we have been told to not open attachments included in an email from someone we don’t know, but this is also true for clicking on links. In many cases, those links do not go to where you are expecting them too. Lets look at a quick example. I have created a simple fake email with some made up business and web site addresses.
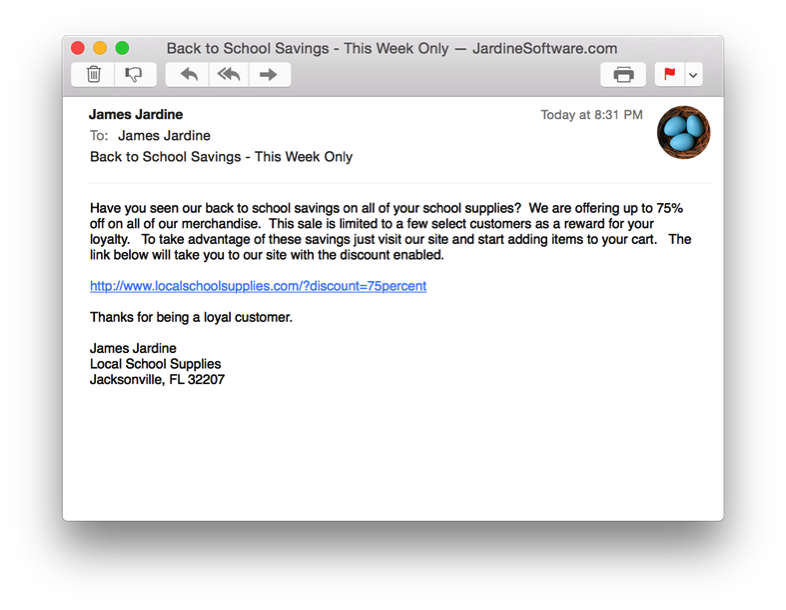
The link in the image above looks normal, however when we take a moment to inspect it more it turns out not to be. To inspect the link, most email clients allow us to hover over it for a moment to see a preview. Hovering means to place your mouse over the link, but don’t click the button. After a few seconds, a balloon should appear to show you what the link actually points to. The following image shows this in action.
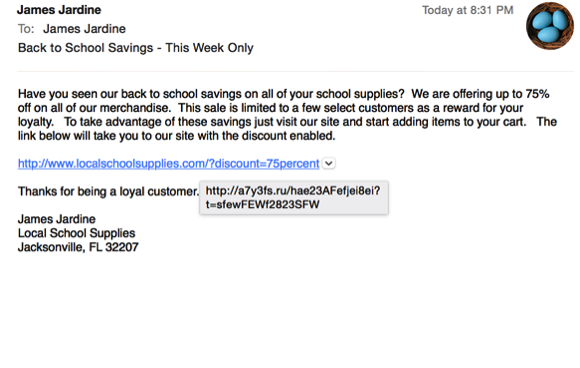
If it is possible, it is recommended to type out the link that is presented or go to the site directly in the browser (if it is a familiar site) rather than clicking on the link. It is understandable that this is not always possible, as some links contain a special discount code or special offer. In these cases, take the time to make sure that the link is going to the site you are expecting. As with any security tip, trust your gut. If something doesn’t seem right, don’t enter any type of personal information with it.
Verify the Site is Using HTTPS
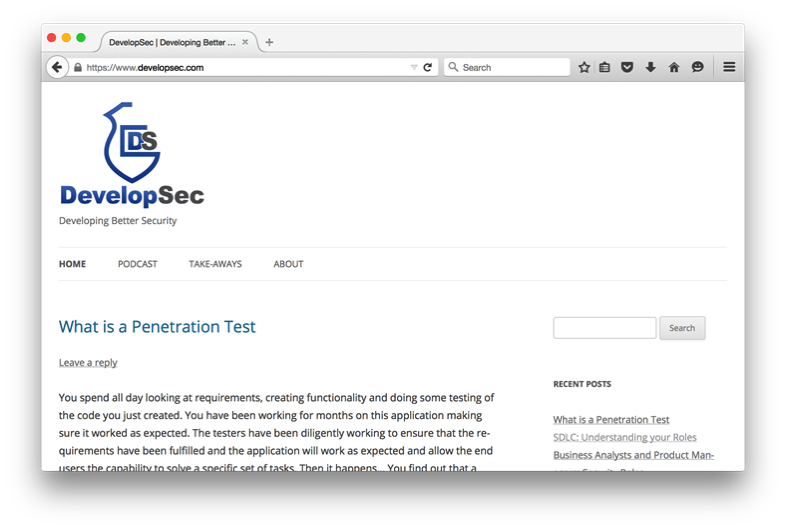
When you are about to use your credit card online, make sure that the web site you are using is using HTTPS. HTTPS means that the information you provide will be encrypted, or protected, as it is sent to the web site. Think of it like using a security envelope vs a regular envelope when sending snail mail. Of course, there are other protections that make it more secure than a security envelope, but that should be a good analogy for most people. There are a few ways to verify this. First, you can look at the address bar in the browser that displays the site name and make sure it starts with “HTTPS”. The next step is to verify that there is a padlock icon near that site address. The image below shows this site and in the top left you will see the padlock icon and https://www.developsec.com. That indicates that the site is using HTTPS and your data will be protected when sent to the business.
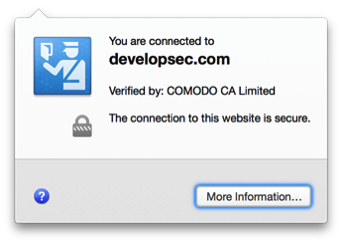
You can also verify even further, by clicking on the padlock (in FireFox) the site name matches up with the certificate name. In the below image you will see that the box that appears states I am connected to developsec.com.
When Searching, Select the Right Site
If you are using Google or Yahoo, or some other favorite search engine, make sure that the search result you click on is the site you are expecting. With how technology is advancing and the way we have updated how search engines work, there are possibly thousands of results that may come back. Search engines also often put ads as the first few results. Take a moment and ensure that you are going where you think you are going. Don’t just click the first link that is returned.
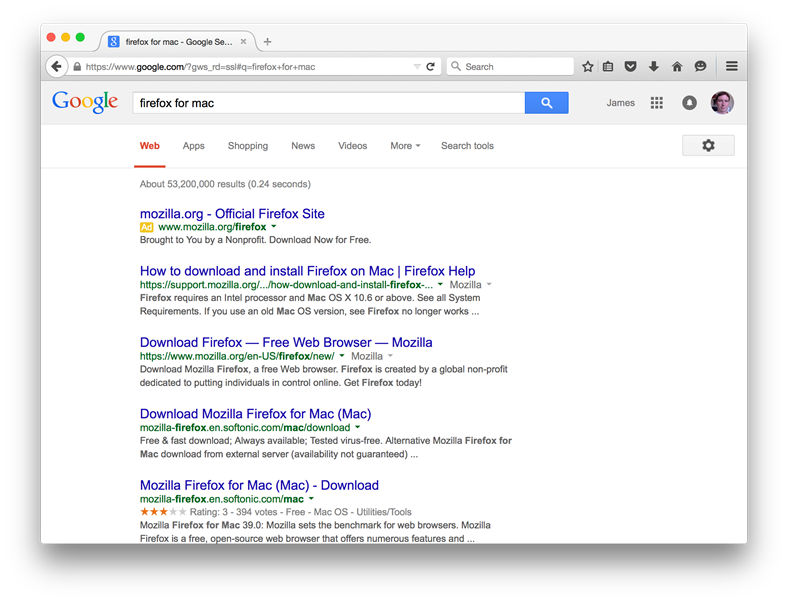
The following image shows a search for FireFox for Mac. Notice how there is an Ad (which does point to the real FireFox download) and then multiple results. The ones that go to Mozilla.org are valid results that go to the creators of FireFox. Under that are results that don’t go to Mozilla.org. While these sites may be valid downloads of FireFox (I did not try them), you want to try and stay with the creators or the software if possible. Often times software is repackaged by other vendors and that repackaging adds in software you may not want.
Trust Your Gut
Security often times comes down to trusting what your gut tells you. If something seems out of place, then it probably is. If you don’t feel comfortable, then don’t input your sensitive information. Researching the item more can also help make a decision. if you are downloading software, do other searches about it to see if people downloaded malicious versions. If it is from a different site than the vendor, do a search to see if anyone else has flagged that download as bad. Finally, if you notice fraudulent charges, make sure you notify your credit card company as soon as possible.
Leave a Reply
You must be logged in to post a comment.