Start reading the news and you are bound to read about another data breach involving user credentials. Whether you get any details about how the passwords (that were stolen) were stored, we can assume that in many of these cases that they were not well protected. Maybe they were stored in clear text (no, it can't be true), or use weak hashes. Passwords hold the key to our access to most applications. What are you doing to help protect them? First, lets just start with recommending that the … [Read more...] about Password Storage Overview
Unsupported Browser Support
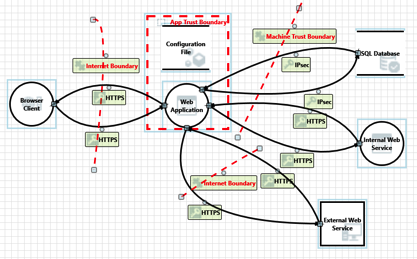
Ok, so the title is a bit counter-intuitive. I recently saw an article talking about the end of support for some of the Internet Explorer versions out there (http://www.computerworld.com/article/3018786/web-browsers/last-chance-to-upgrade-ie-or-switch-browsers-as-microsofts-mandate-looms.html) and got to thinking about the number of sites that still require supporting some of these older versions of browsers. This is typically more common in the big corporate enterprises, as they have the … [Read more...] about Unsupported Browser Support
Untrusted Data: Quick Overview
In the application security community it is common to talk about untrusted data. Talk about any type of injection attack (SQLi, XSS, XXE, etc) and one of the first terms mentions is untrusted data. In some cases it is also known as user data. While we hear the phrase all the time, are we sure everyone understands what it means? What is untrusted data? It is important that anyone associated with creating and testing applications understand the concept of untrusted data. Unfortunately, it can … [Read more...] about Untrusted Data: Quick Overview
Insufficient Session Expiration: Testing
Insufficient Session Timeout is a security flaw that can mean a few different things. One common finding for this is that the session timeout is set too long. For example, the session is valid after an hour of being idle. Another common finding is when the session is not properly terminated after the user uses the logout/sign out feature. In this post we will cover these two test cases and how to test for them. A.K.A Insufficient Logout Insecure Logout Insufficient Session … [Read more...] about Insufficient Session Expiration: Testing
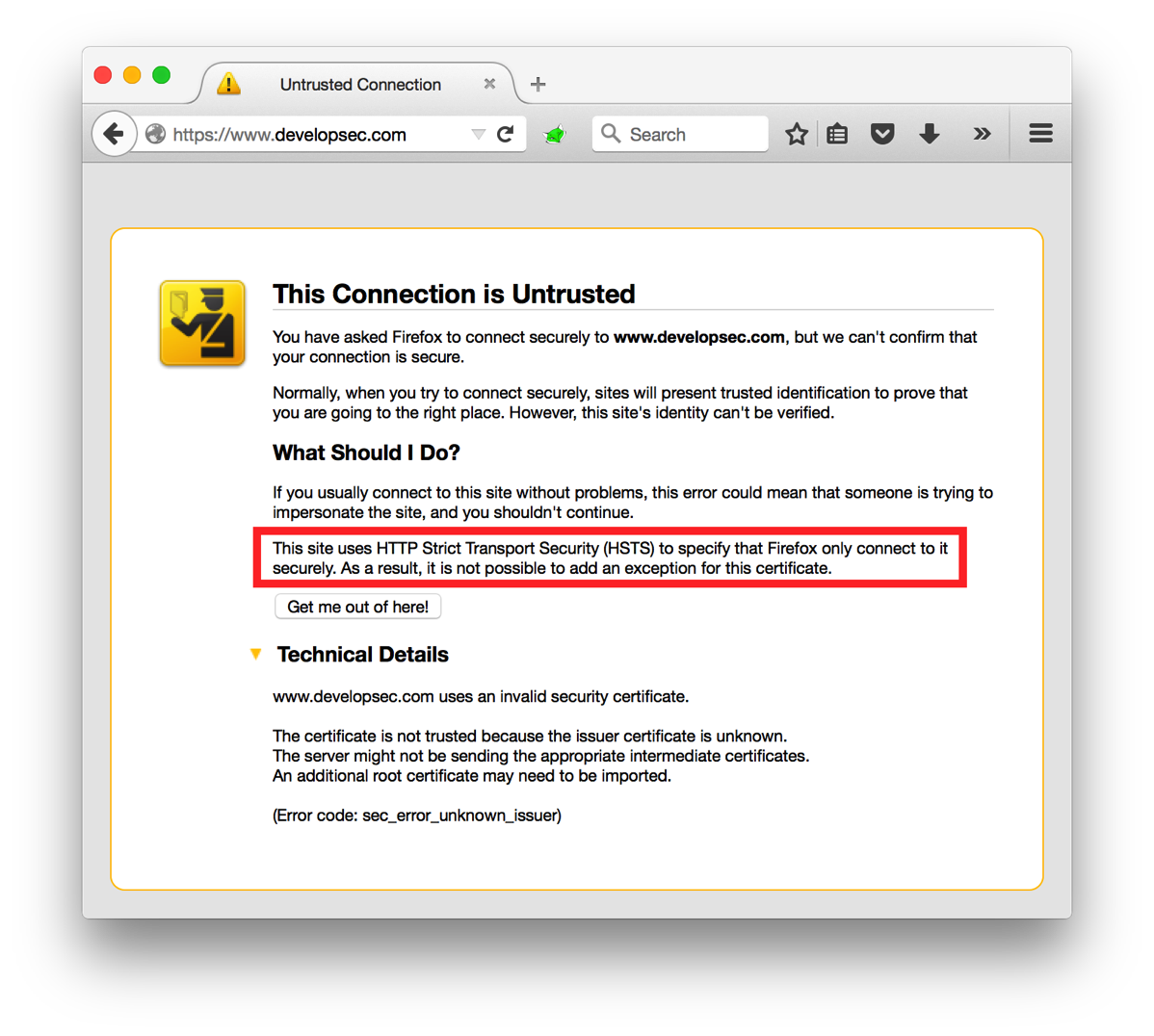
HTTP Strict Transport Security (HSTS): Overview
A while back I asked the question "Is HTTP being left behind for HTTPS?". If you are looking to make the move to an HTTPS only web space one of the settings you can configure is HTTP Strict Transport Security, or HSTS. The idea behind HSTS is that it will tell the browser to only communicate with the web site over a secure channel. Even if the user attempts to switch to HTTP, the browser will make the change before it even sends the request. HSTS is implemented as a response header with a … [Read more...] about HTTP Strict Transport Security (HSTS): Overview
HIV clinic Data Breach: Thoughts and Takeaways
One of the most common ways for sensitive information to be released outside of an authorized environment is by simple, common mistakes made by employees. These types of incidents usually have no malicious intent and are generally innocent in nature. An example of this was recently reported regarding a newsletter that was sent out to HIV patients (and others) that the sender made a simple mistake. Rather than use the BCC for each recipients address, they used the CC field. For those that may … [Read more...] about HIV clinic Data Breach: Thoughts and Takeaways