Open any social media platform or pull up any mainstream media and undoubtably, you have seen many posts/articles talking about the log4j vulnerability. If you haven't seen this, here is a quick link to catch up https://snyk.io/blog/log4j-rce-log4shell-vulnerability-cve-2021-4428/. This post is not going to be about log4j, nor is it going to go into any of the details the thousands of others articles out there would go through. Instead, I want to discuss this at a higher level. Log4j is just an … [Read more...] about Log4J – Reflection and Progression
3rd party component
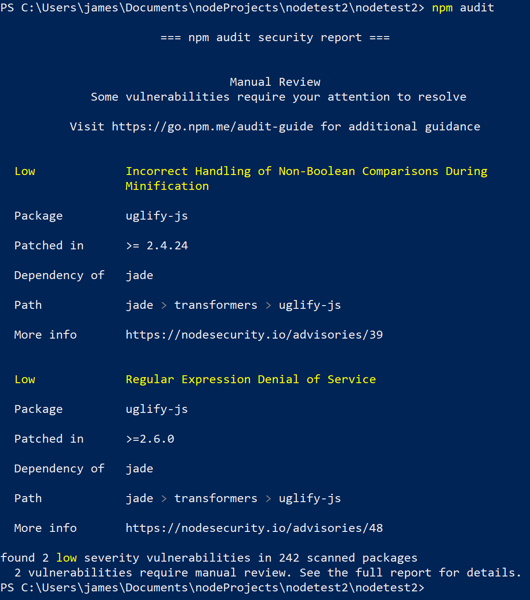
Checking npm packages using npm-audit
Our applications rely more and more on external packages to enable quick deployment and ease of development. While these packages help reduce the code we have to write ourselves, it still may present risk to our application. If you are building Nodejs applications, you are probably using npm to manage your packages. For those that don't know, npm is the node package manager. It is a direct source to quickly include functionality within your application. For example, say you want to hash your … [Read more...] about Checking npm packages using npm-audit
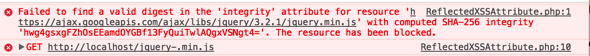
Sub Resource Integrity – SRI
Do you rely on content distribution networks or CDNs to provide some of your resources? You may not consider some of your resources in this category, but really it is any resource that is provided outside of your server. For example, maybe you pull in the jQuery JavaScript file from ajax.googleapis.com rather than hosting the file on your server. These CDNs provide a great way to give fast access to these resources. But how do you know you are getting the file you expect? As an … [Read more...] about Sub Resource Integrity – SRI
ImageMagick – Take-aways
Do your applications accept file uploads? More specifically, image uploads? Do you use a site that allows you to upload images? If you haven't been following the news lately, there was recently a few vulnerabilities found in the ImageMagick image library. This library is very common in websites to perform image processing. The vulnerability allows remote code execution (RCE) on the web server, which is very dangerous. For more specific details on the vulnerability itself, check out this … [Read more...] about ImageMagick – Take-aways