Cross-Site Scripting flaws, as well as other injection flaws, are pretty well understood. We know how they work and how to mitigate them. One of the key factors in mitigation of these flaws is output encoding or escaping. For SQL, we escape by using parameters. For cross-site scripting we use context sensitive output encoding. In this post, I don’t want to focus on the how of output encoding for cross-site scripting. Rather, I want to focus on when in the pipeline it should be done. Over … [Read more...] about Properly Placing XSS Output Encoding
application security
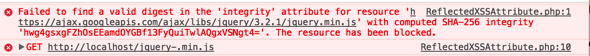
Sub Resource Integrity – SRI
Do you rely on content distribution networks or CDNs to provide some of your resources? You may not consider some of your resources in this category, but really it is any resource that is provided outside of your server. For example, maybe you pull in the jQuery JavaScript file from ajax.googleapis.com rather than hosting the file on your server. These CDNs provide a great way to give fast access to these resources. But how do you know you are getting the file you expect? As an … [Read more...] about Sub Resource Integrity – SRI
Using the AWS disruption to your advantage
By now you have heard of the amazon issues that plagued many websites a few days ago. I want to talk about one key part of the issue that often gets overlooked. If you read through their message describing their service disruption (https://aws.amazon.com/message/41926/) you will notice a section where they discuss some changes to the tools they use to manage their systems. So let's take a step back for a moment. Amazon attributed the service disruption to basically a simple mistake … [Read more...] about Using the AWS disruption to your advantage
Security Tips for Copy/Paste of Code From the Internet
Developing applications has long involved using code snippets found through textbooks or on the Internet. Rather than re-invent the wheel, it makes sense to identify existing code that helps solve a problem. It may also help speed up the development time. Years ago, maybe 12, I remember a co-worker that had a SQL Injection vulnerability in his application. The culprit, code copied from someone else. At the time, I explained that once you copy code into your application it is now your … [Read more...] about Security Tips for Copy/Paste of Code From the Internet
Gmail will block JavaScript file attachments
According to a recent announcement, Gmail will start blocking .js file attachments starting February 13, 2017. Blocking specific attachment types isn't something that is new to Gmail. They already block attaching file attachments that are .exe, .msc, and .bat types. The recent move to add javascript files is most likely related to the recent malware/ransomware campaigns that have started using JavaScript files instead of Microsoft Office files. There was an article posted back in April … [Read more...] about Gmail will block JavaScript file attachments
Secure Notification Updates in FireFox and Chrome
There has been a steady increase in the number of applications that have switched to using HTTPS instead of HTTP for communication. Even sites that have no sensitive information or authentication mechanisms. Using HTTPS provides authentication and a secure channel to transmit data between client and server. The authentication verifies that you are communicating with the organization you thought you were. This secure transmission is meant to stop other parties from being able to read or … [Read more...] about Secure Notification Updates in FireFox and Chrome