It is possible to put a custom login page up for the Serv-U login screen. When this happens, the page is most likely not displaying the version number. One way that may help identify the version is to visit the Mobile login page at /Web Client/Mobile/MLogin.htm. Why is this important? When performing external security scans with tools like Nessus, it may report that the version of Serv-U is incorrect. Finding the version number is important in identifying potential false positives. … [Read more...] about How Can I Find The Version of Serv-U FTP on Custom Branded Login?
pen test
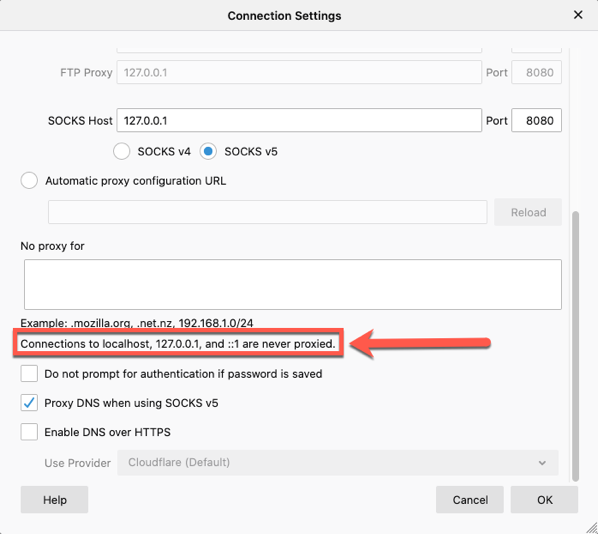
Proxying localhost on FireFox
When you think of application security testing, one of the most common tools is a web proxy. Whether it is Burp Suite from Portswigger, ZAP from OWASP, Fiddler, or Charles Proxy, a proxy is heavily used. From time to time, you may find yourself testing a locally running application. Outside of some test labs or local development, this isn't really that common. But if you do find yourself testing a site on localhost, you may run into a roadblock in your browser. If you are using a recent version … [Read more...] about Proxying localhost on FireFox
Thinking about starting a bug bounty? Do this first.
Application security has become an important topic within our organizations. We have come to understand that the data that we deem sensitive and critical to our business is made available through these applications. With breaches happening all the time, it is critical to take reasonable steps to help protect that data by ensuring that our applications are implementing strong controls. Over the years, testing has been the main avenue for "implementing" security into applications. We have seen a … [Read more...] about Thinking about starting a bug bounty? Do this first.
What is a Penetration Test
You spend all day looking at requirements, creating functionality and doing some testing of the code you just created. You have been working for months on this application making sure it worked as expected. The testers have been diligently working to ensure that the requirements have been fulfilled and the application will work as expected and allow the end users the capability to solve a specific set of tasks. Then it happens... You find out that a penetration test is coming. … [Read more...] about What is a Penetration Test