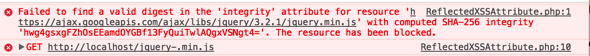
Do you rely on content distribution networks or CDNs to provide some of your resources? You may not consider some of your resources in this category, but really it is any resource that is provided outside of your server. For example, maybe you pull in the jQuery JavaScript file from ajax.googleapis.com rather than hosting the file on your server. These CDNs provide a great way to give fast access to these resources. But how do you know you are getting the file you expect? As an … [Read more...] about Sub Resource Integrity – SRI
secure design
Remember Me Features
Tired of constantly logging into your applications? Don't you wish they would just remember you each time you visit, logging you right in? It isn't as always easy to achieve such a status. There are multiple ways remember me can be implemented. Lets take a look at some of them. Remember UserName One of the most common ways for a site to implement the remember me functionality is to remember the username only. The username is typically stored in a cookie on the client's computer. … [Read more...] about Remember Me Features
MongoDBs under attack from ransomware
In recent news, it was identified that MongoDB databases are being exposed on the internet and infected with ransomeware. In a little under a week, the infection count went from 200 to 10,000. That is a quick ramp up. In this case, misconfigurations may bind the database port to the public interface, while also allowing anonymous access. This combination can be devastating. Doing a quick search on Shodan you may find there are thousands of misconfigured MondoDB servers exposed on the … [Read more...] about MongoDBs under attack from ransomware
The 1 thing you need to know about the Daily Motion hack
It was just released that Daily Motion suffered a hack attack resulting in a large number of usernames and email addresses being released. Rather than focusing on the number of records received (the wow factor), I want to highlight what most places are just glancing over: Password Storage. According to the report, only a small portion of the accounts had a password associated with it. That is in the millions, and you might be thinking this is bad. It is actually the highlight of the story. … [Read more...] about The 1 thing you need to know about the Daily Motion hack
Insulin Pump Vulnerability – Take-aways
It was recently announced that there were a few vulnerabilities found with some insulin pumps that could allow a remote attacker to cause the pump to distribute more insulin than expected. There is a great write up of the situation here. When I say remote attack, keep in mind that in this scenario, it is someone that is within close proximity to the device. This is not an attack that can be performed via the Internet. This situation creates an excellent learning opportunity for anyone that … [Read more...] about Insulin Pump Vulnerability – Take-aways
How Serious is Username Enumeration
Looking through Twitter recently, I caught a very interesting stream that started with the following message: What's the deal with the enumeration exclusions on all the @bugcrowd bounties. Clients just don't want to fix?— Stephen Haywood (@averagesecguy) July 26, 2016 There were quite a few replies, and a good discussion on the topic of the seriousness of username enumeration flaws. 140 characters is difficult to share a lot of thoughts, so I thought this would actually be … [Read more...] about How Serious is Username Enumeration