A vulnerability was just identified in your website. How would you know? The process of vulnerability disclosure to an organization is often very difficult to identify. Whether you are offering any type of bounty for security bugs or not, it is important that there is a clear path for someone to notify you of a potential concern. Unfortunately, the process is different on every application and it can be very difficult to find it. For someone that is just trying to help out, it can be very … [Read more...] about Overview of Web Security Policies
secure development
Ep. 101: You’re not always right and that is ok
In this episode, James shares a story of learning from a mistake and how we can't be right every time. Hear what he learned and how you can learn too. For more info go to https://www.developsec.com or follow us on twitter (@developsec). DevelopSec provides application security consulting and training to add value to your application security program. Contact us today to see how we can help. … [Read more...] about Ep. 101: You’re not always right and that is ok
Ep. 100: Choosing Security Tools
In this episode we talk about choosing the right security tools for your environment. There are lots of vendors offering solutions to help identify security issues within our applications. The trick is to learn to identify which ones make the most sense for your environment. For more info go to https://www.developsec.com or follow us on twitter (@developsec). DevelopSec provides application security consulting and training to add value to your application security program. Contact us today to … [Read more...] about Ep. 100: Choosing Security Tools
Choosing Application Security Tools
There are lots of security tools available, so how do you know which one to pick? If your security team is not including the application teams in the decision, you run a big risk of failure. The security team does get the ability to form relationships with vendors. We see them at conferences. We know people that work there. Because our focus is on security, we know the tools that exist in our space and we have an idea of which ones may be better than others. Of course, this is often due to … [Read more...] about Choosing Application Security Tools
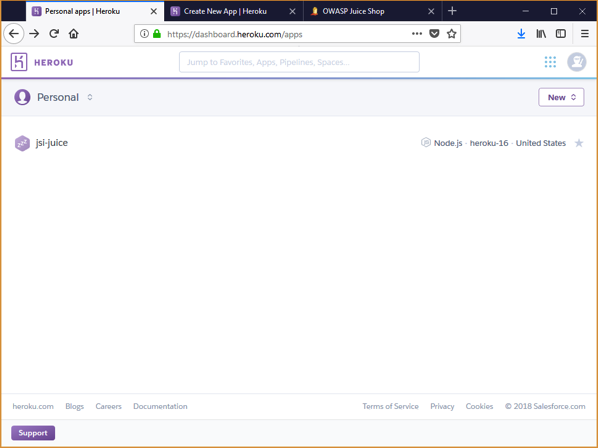
Installing OWASP JuiceShop with Heroku
I am often asked the question by clients and students where people can go to learn hacking techniques for application security. For years, we have had many purposely vulnerable applications available to us. These applications provide a safe environment for us to learn more about hacking applications and the vulnerabilities that are exposed without the legal ramifications. In this post I want to show you how simple it is to install the OWASP Juice Shop application using Heroku. Juice Shop is a … [Read more...] about Installing OWASP JuiceShop with Heroku
Installing OWASP JuiceShop with Docker
I am often asked the question by clients and students where people can go to learn hacking techniques for application security. For years, we have had many purposely vulnerable applications available to us. These applications provide a safe environment for us to learn more about hacking applications and the vulnerabilities that are exposed without the legal ramifications. In this post I want to show you how simple it is to install the OWASP Juice Shop application using a Docker container. … [Read more...] about Installing OWASP JuiceShop with Docker