Building applications today includes the use of some pretty impressive platforms. These platforms have so much built in capability, many of the most common tasks are easily accomplished through simple method calls. As developers, we rely on these frameworks to provide a certain level of functionality. Much of which we may never even use. When it comes to security, the platform can be a love/hate relationship. On the one hand, developers may have little control over how the platform handles … [Read more...] about Understanding Your Application Platform
secure development
MySpace Account Takeover – Take-aways
Have you ever forgotten your password, or lost access to your accounts? I know I have. The process of getting your access back can range from very easy to quite difficult. In one case, I had an account that required that a pin code be physically mailed to me in 7-10 days. Of course, this was a financial account that required extra protections. I came across this article (https://www.wired.com/story/myspace-security-account-takeover/) that identified that MySpace's process for regaining access … [Read more...] about MySpace Account Takeover – Take-aways
Validation: Client vs. Server
Years ago, I remember being on a technical interview phone call for a senior developer position. What stood out was when the interviewer asked me about performing input validation. The question was in regards to if validation should be on the client or the server. My answer: The server. What took me by surprise was when the response was that my answer was incorrect. In fact, I was told that Microsoft recommends performing validation on the client. This was inaccurate information, but I let it … [Read more...] about Validation: Client vs. Server
Properly Placing XSS Output Encoding
Cross-Site Scripting flaws, as well as other injection flaws, are pretty well understood. We know how they work and how to mitigate them. One of the key factors in mitigation of these flaws is output encoding or escaping. For SQL, we escape by using parameters. For cross-site scripting we use context sensitive output encoding. In this post, I don’t want to focus on the how of output encoding for cross-site scripting. Rather, I want to focus on when in the pipeline it should be done. Over … [Read more...] about Properly Placing XSS Output Encoding
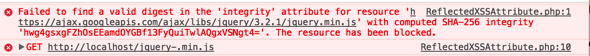
Sub Resource Integrity – SRI
Do you rely on content distribution networks or CDNs to provide some of your resources? You may not consider some of your resources in this category, but really it is any resource that is provided outside of your server. For example, maybe you pull in the jQuery JavaScript file from ajax.googleapis.com rather than hosting the file on your server. These CDNs provide a great way to give fast access to these resources. But how do you know you are getting the file you expect? As an … [Read more...] about Sub Resource Integrity – SRI
Using the AWS disruption to your advantage
By now you have heard of the amazon issues that plagued many websites a few days ago. I want to talk about one key part of the issue that often gets overlooked. If you read through their message describing their service disruption (https://aws.amazon.com/message/41926/) you will notice a section where they discuss some changes to the tools they use to manage their systems. So let's take a step back for a moment. Amazon attributed the service disruption to basically a simple mistake … [Read more...] about Using the AWS disruption to your advantage