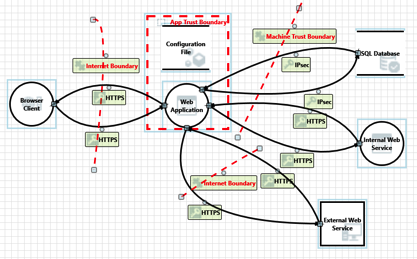
You have been working hard for the past few weeks or months on the latest round of features for your flagship product. You are excited. The team is excited. Then a security test identifies a vulnerability. Balloons deflate and everyone starts to scramble. Take a breath. Not all vulnerabilities are created equal and the risk that each presents is vastly different. The organization should already have a process for triaging security findings. That process should be assessing the risk of the … [Read more...] about Does the End of an Iteration Change Your View of Risk?
security
Sharing with Social Media
Does your application provide a way for users to share their progress or success with others through social media? Are you thinking about adding that feature in the future? Everyone loves to share their stories with their friends and colleagues, but as application developers we need to make sure that we are considering the security aspects of how we go about that. Take-Aways Use the APIs when talking to another service Don't accept credentials to other systems out of your control Check … [Read more...] about Sharing with Social Media
Unsupported Browser Support
Ok, so the title is a bit counter-intuitive. I recently saw an article talking about the end of support for some of the Internet Explorer versions out there (http://www.computerworld.com/article/3018786/web-browsers/last-chance-to-upgrade-ie-or-switch-browsers-as-microsofts-mandate-looms.html) and got to thinking about the number of sites that still require supporting some of these older versions of browsers. This is typically more common in the big corporate enterprises, as they have the … [Read more...] about Unsupported Browser Support
Untrusted Data: Quick Overview
In the application security community it is common to talk about untrusted data. Talk about any type of injection attack (SQLi, XSS, XXE, etc) and one of the first terms mentions is untrusted data. In some cases it is also known as user data. While we hear the phrase all the time, are we sure everyone understands what it means? What is untrusted data? It is important that anyone associated with creating and testing applications understand the concept of untrusted data. Unfortunately, it can … [Read more...] about Untrusted Data: Quick Overview
HTTP Strict Transport Security (HSTS): Overview
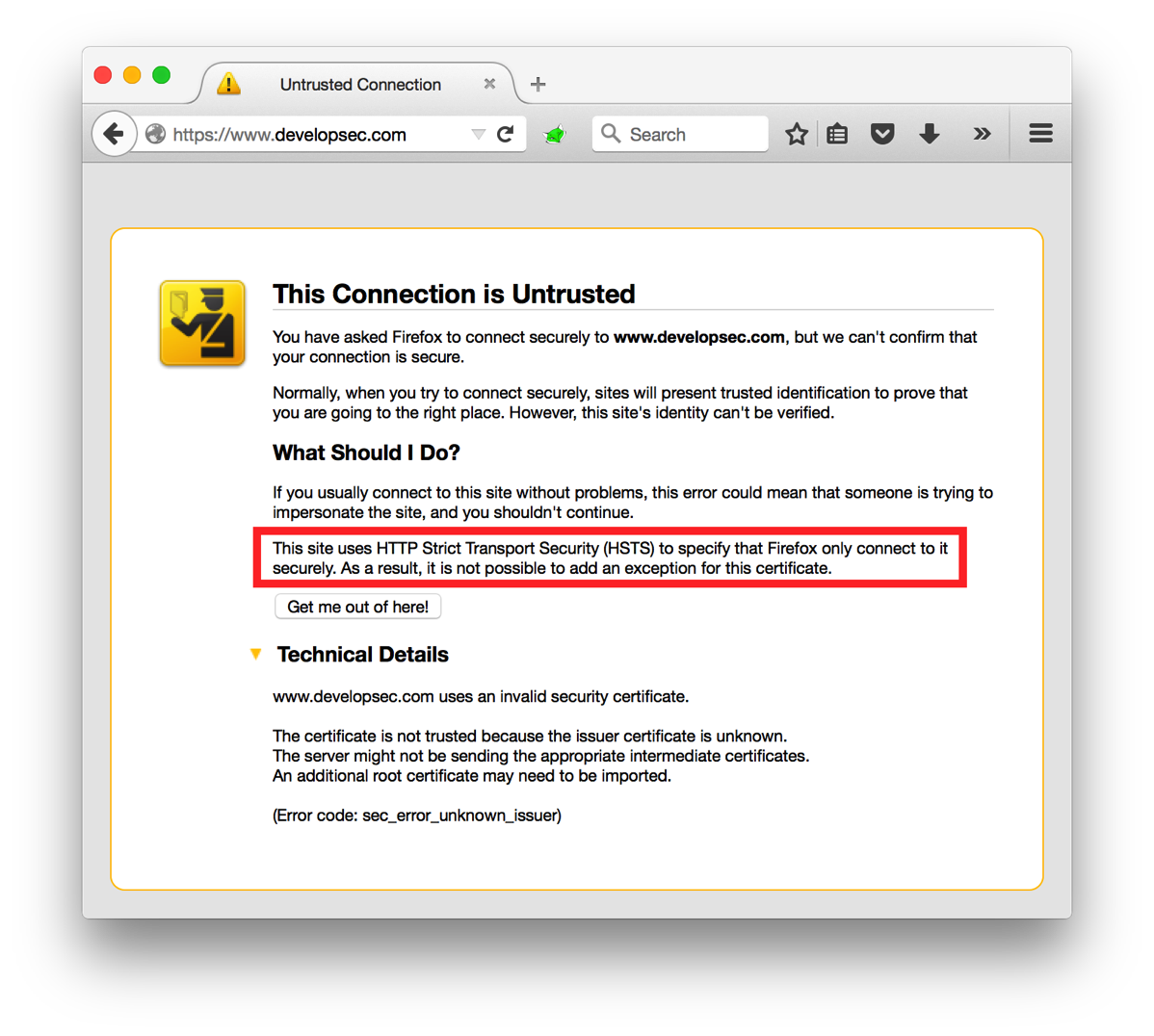
A while back I asked the question "Is HTTP being left behind for HTTPS?". If you are looking to make the move to an HTTPS only web space one of the settings you can configure is HTTP Strict Transport Security, or HSTS. The idea behind HSTS is that it will tell the browser to only communicate with the web site over a secure channel. Even if the user attempts to switch to HTTP, the browser will make the change before it even sends the request. HSTS is implemented as a response header with a … [Read more...] about HTTP Strict Transport Security (HSTS): Overview
HIV clinic Data Breach: Thoughts and Takeaways
One of the most common ways for sensitive information to be released outside of an authorized environment is by simple, common mistakes made by employees. These types of incidents usually have no malicious intent and are generally innocent in nature. An example of this was recently reported regarding a newsletter that was sent out to HIV patients (and others) that the sender made a simple mistake. Rather than use the BCC for each recipients address, they used the CC field. For those that may … [Read more...] about HIV clinic Data Breach: Thoughts and Takeaways