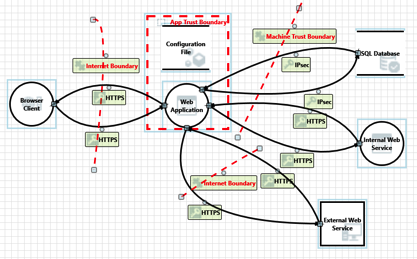
When it comes to creating applications, there is a need for multiple environments to support the development process. It typically starts on the developers own computer, then on to an integration environment, a QA testing environment, possibly a UAT (User Acceptance Testing) environment, and then finally production. Depending on your organization, you may have some, none, or all of these different environments. When it comes to security, the focus is typically on the production environment. … [Read more...] about Security in Testing Environments
testing
When One Testing Solution Isn’t Enough
Go to any conference, attend some webinars, or just do a search for application security testing solutions and you can quickly see the sheer number of solutions out there. As in every situation, there are some that are great and some that are not so great. With such great marketing, it is often very difficult to determine what is the best solution. All too often people are looking for that silver bullet. That one testing tool or pen testing company that will find everything. Unfortunately, … [Read more...] about When One Testing Solution Isn’t Enough
Unsupported Browser Support
Ok, so the title is a bit counter-intuitive. I recently saw an article talking about the end of support for some of the Internet Explorer versions out there (http://www.computerworld.com/article/3018786/web-browsers/last-chance-to-upgrade-ie-or-switch-browsers-as-microsofts-mandate-looms.html) and got to thinking about the number of sites that still require supporting some of these older versions of browsers. This is typically more common in the big corporate enterprises, as they have the … [Read more...] about Unsupported Browser Support
Untrusted Data: Quick Overview
In the application security community it is common to talk about untrusted data. Talk about any type of injection attack (SQLi, XSS, XXE, etc) and one of the first terms mentions is untrusted data. In some cases it is also known as user data. While we hear the phrase all the time, are we sure everyone understands what it means? What is untrusted data? It is important that anyone associated with creating and testing applications understand the concept of untrusted data. Unfortunately, it can … [Read more...] about Untrusted Data: Quick Overview
Insufficient Session Expiration: Testing
Insufficient Session Timeout is a security flaw that can mean a few different things. One common finding for this is that the session timeout is set too long. For example, the session is valid after an hour of being idle. Another common finding is when the session is not properly terminated after the user uses the logout/sign out feature. In this post we will cover these two test cases and how to test for them. A.K.A Insufficient Logout Insecure Logout Insufficient Session … [Read more...] about Insufficient Session Expiration: Testing
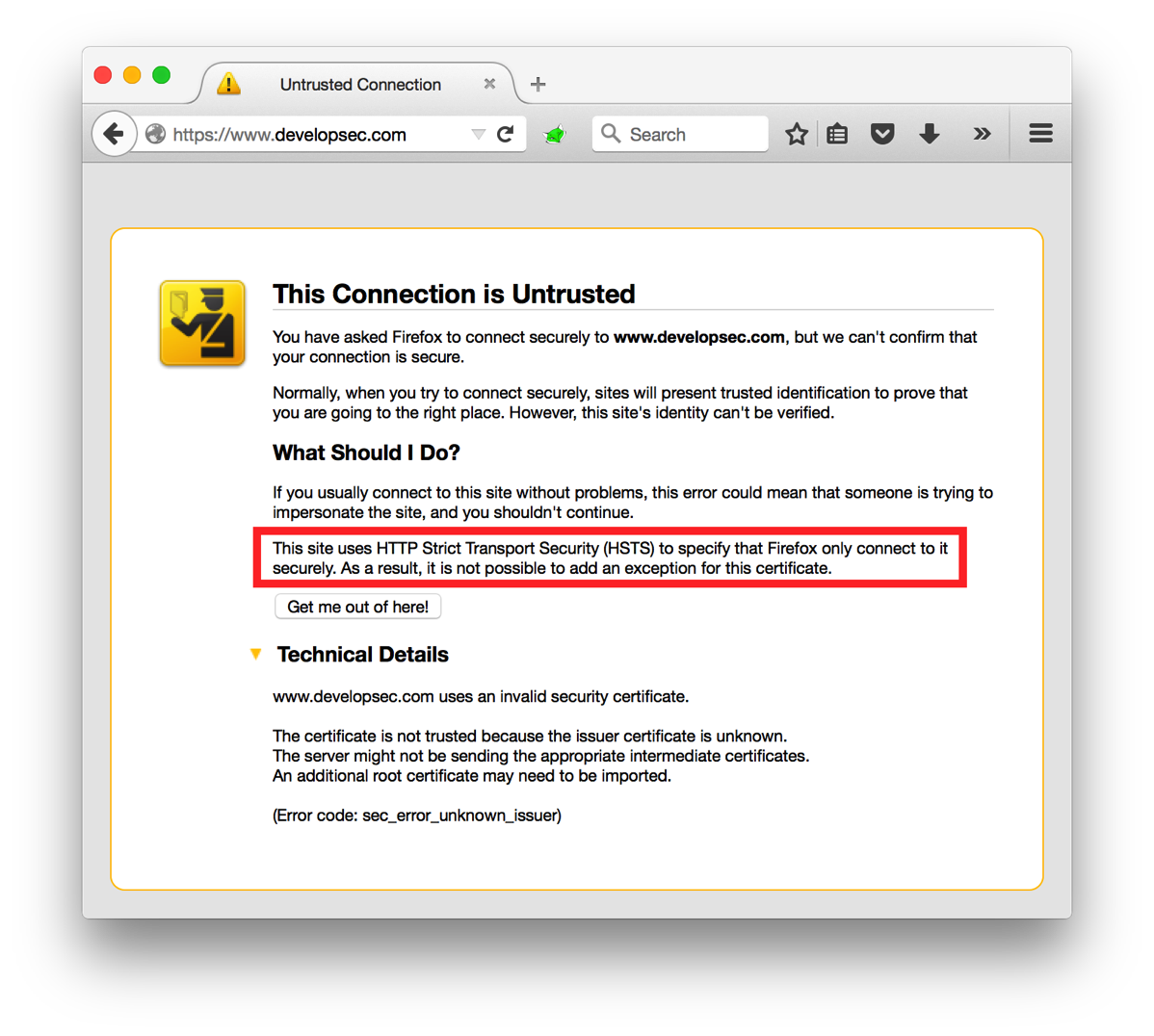
HTTP Strict Transport Security (HSTS): Overview
A while back I asked the question "Is HTTP being left behind for HTTPS?". If you are looking to make the move to an HTTPS only web space one of the settings you can configure is HTTP Strict Transport Security, or HSTS. The idea behind HSTS is that it will tell the browser to only communicate with the web site over a secure channel. Even if the user attempts to switch to HTTP, the browser will make the change before it even sends the request. HSTS is implemented as a response header with a … [Read more...] about HTTP Strict Transport Security (HSTS): Overview